Troubleshoot TLS 1.2 with Elliptic-curve cryptography in SAP PO
Updated: 7/22/2024 - Symptom: "Error during ping operation:Error while silently connecting: org.w3c.www.protocol.http.HttpException: Peer sent alert: Alert Fatal: handshake failure", SAP note 3424764
At the time of writing this blog – Election week 2020, Confluent Cloud Shema Registry using Let’s Encrypt to sign the certificates for Schema Registry (HTTPS endpoint), it uses TLS 1.2, ECDHE_RSA with P-256, and AES_256_GCM.
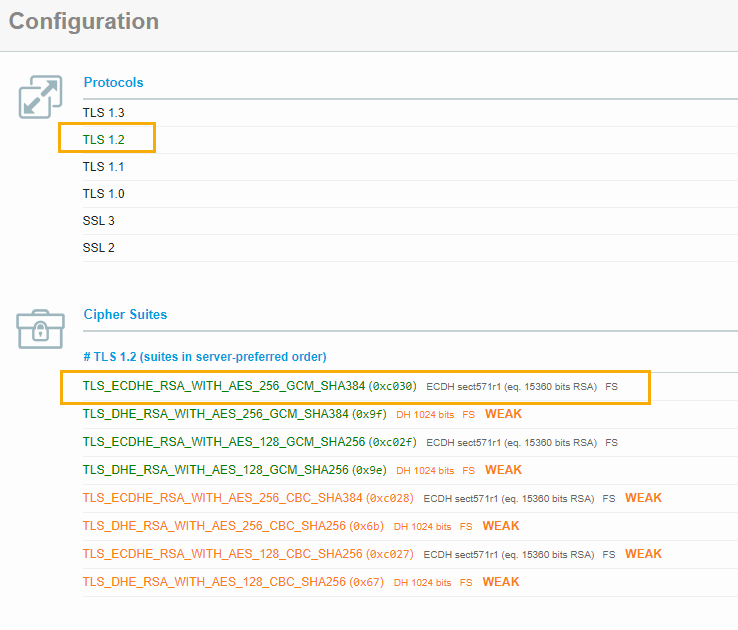
And it’s not working with SAP PO 7.5 latest SP 19. There is a list of default cipher suites, but it’s not including the one above. For more information or those steps below not working, refer to this note 2284059.
The solution is to update the cipher suits list. Follow these steps:
1. Identify the problem. Follow this note 2616423
2. Make sure the JCE policy files on the server are unlimited. Follow this note 1240081
3. Add a system property “iaik.security.ssl.configFile” to point custom-defined cipher suites. Follow this note 2708581
4. Restart Java AS to get the new system property effect.
Implementation Steps:
Note: Don’t forget to import certs chain of the target endpoint to the Netweaver Keystore.
1. Identify the problem
- Identify the certificate of the request endpoint.
Using Chrome Developer Tool (Ctrl + Shift + I)
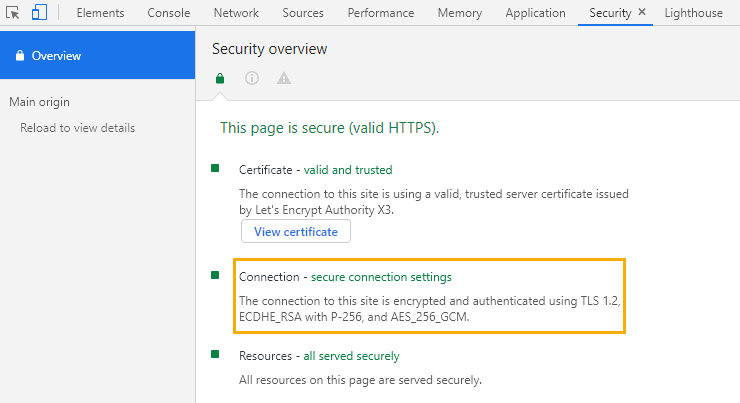
Or from website https://www.ssllabs.com/ssltest/index.html
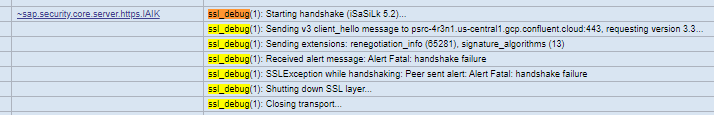
- With an error of handshake in SAP PO trace or XPI Inspector – start XPI Inspector and then trigger a request message to the target endpoint.
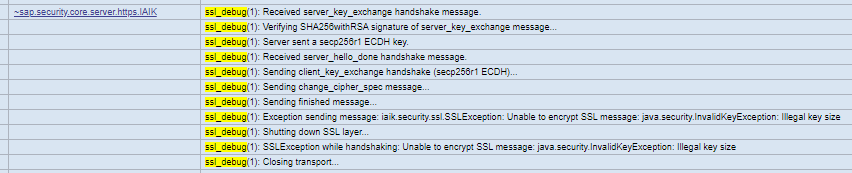
SSLException: Peer sent alert: Alert Fatal: handshake failure
Or error of limited JCE policy
Unable to encrypt SSL message: java.security.InvalidKeyException: Illegal key size
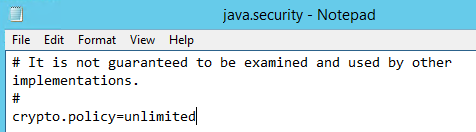
2. Edit/Validate file java.security to the JCE policy unlimited
\usr\sap\<SID>\SYS\exe\jvm\<platform>\sapjvm_8.1.065\sapjvm_8\jre\lib\security
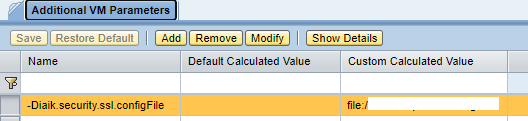
3. Add property “Diaik.security.ssl.configFile”
Create a file SSLContext.properties – place at anywhere in the server.
#
client.allowLegacyRenegotiation=true
extension=signature_algorithms
extension=server_name.noncritical
extension=elliptic_curves
extension=ec_point_formats
securityProvider=iaik.security.ssl.ECCelerateProvider
#
# enable cipher suites with ECDHE key exchange (unlimited strength)
cipherSuite=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
cipherSuite=TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
cipherSuite=TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
cipherSuite=TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256
cipherSuite=TLS_ECDHE_RSA_WITH_CAMELLIA_128_GCM_SHA256
cipherSuite=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
cipherSuite=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
cipherSuite=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
cipherSuite=TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384
cipherSuite=TLS_ECDHE_RSA_WITH_CAMELLIA_256_GCM_SHA384
#
# keep default cipher suites as fallback
cipherSuite=TLS_RSA_WITH_AES_128_GCM_SHA256
cipherSuite=TLS_RSA_WITH_AES_128_CBC_SHA
cipherSuite=TLS_RSA_WITH_AES_128_CBC_SHA256
cipherSuite=TLS_RSA_WITH_CAMELLIA_128_GCM_SHA256
cipherSuite=TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
cipherSuite=TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256
cipherSuite=TLS_RSA_WITH_AES_256_GCM_SHA384
cipherSuite=TLS_RSA_WITH_AES_256_CBC_SHA
cipherSuite=TLS_RSA_WITH_AES_256_CBC_SHA256
cipherSuite=TLS_RSA_WITH_CAMELLIA_256_GCM_SHA384
cipherSuite=TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
cipherSuite=TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256
cipherSuite=SSL_RSA_WITH_3DES_EDE_CBC_SHA
cipherSuite=SSL_RSA_WITH_RC4_128_SHA
#
# enable old&slow DHE cipher suites (you don't want them with limited strength 1024-bit DHE at all)
cipherSuite=TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
cipherSuite=TLS_DHE_RSA_WITH_AES_128_CBC_SHA
cipherSuite=TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
cipherSuite=TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
cipherSuite=TLS_DHE_RSA_WITH_AES_256_CBC_SHA
cipherSuite=TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
Add System property – NWA > Configuration > Infrastructure > Java System Properties > Additional VM Parameters
WINDOWS
-Diaik.security.ssl.configFile=file:/d:/tmp/SSLContext.properties
UNIX
-Diaik.security.ssl.configFile=file:/tmp/SSLContext.properties
4. The restart Java AS.